Network Perimeter
The first line of defense for a network is at its perimeter. The computer at the perimeter forming the defense may be a general-purpose computer, or a special-purpose computer like a router. In either case, there are several functions the perimeter computer may serve to block incoming worms.
Two functions, firewalls and intrusion detection systems, are presented in their "pure" form below; in practice, the perimeter computer may perform both of these functions and more.
Firewalls
A firewall is software which filters incoming network traffic to a network; if the software runs on a computer dedicated to this task, then that computer is also referred to as a firewall. Firewall software can be run on a perimeter computer, a host computer, or both.
Each network packet in the traffic has two basic parts, header and data. This is analogous to sending a letter: the envelope has the addresses of the letter's sender and receiver, and the letter's contents are sealed inside the envelope.
A packet's header has the sender and receiver information, and its data contains the packet contents that are meant for the recipient. Basic firewalls filter network packets based on header information:
- The source IP address, or the computer that the packet purportedly comes from.
- The source port. Each computer has a fixed number of virtual "ports" for communication; the combination of an IP address and port identifies a communications endpoint.
- The IP address of the computer where the packet is destined.
- The destination port. The network servers providing services usually reside at well-known port numbers, so that a computer trying to contact a service knows where to direct its request.
- The protocol type. Filtering on the protocol type results in a very coarsegrained discrimination between different traffic types: connection-based (TCP), connectionless (UDP), and low-level control messages (ICMP).
A firewall will have a set of rules which describe the policy it should implement - in other words, which packets it should pass through, and which packets it should drop. A firewall could look at a packet's data too, called deep packet inspection, but the format and semantics of the data depend on exactly where the packet is going.
Making sense of the packet data would require the firewall to understand the language of every network service, and doing so would both slow and complicate a firewall, just like opening and reading a letter is slower and more complicated than glancing at its envelope.
As a worm defense, a firewall provides a similar function to limiting available network services. A firewall prevents a worm from communicating with, and possibly exploiting, vulnerable network servers.
It only defends against outside attacks, so any worm that makes it past the firewall (e.g., an email worm that a user runs on their computer behind the firewall) can operate with impunity.
Intrusion Detection Systems
An intrusion detection system analyzes incoming network traffic, performing deep packet inspection to watch for packets or sequences of packets that signal attacks. Like firewalls, intrusion detection systems can run on the perimeter computer or a host computer.
Like criminals, intrusion detection systems go by a wide variety of names:
- Intrusion detection systems (IDS).
- Host intrusion detection systems (HIDS), for host-based IDS.
- Network intrusion detection systems (NIDS), for network-based IDS. These need not only be at the network perimeter. IDS (and firewalls) may also be deployed internally to a network, to add extra worm protection for critical internal subnets.
- Intrusion prevention systems (IPS). "Prevention" implies that an attack is thwarted rather than just noticed. Although there are no commonly agreedupon definitions, an IPS would imply a system that filters traffic like a firewall, but that is able to do deep packet inspection like an IDS. In contrast, an IDS doesn't filter traffic, only watches it and raises an alarm if suspicious activity is found.
For worms, an intrusion detection system can either look for the signatures of known worms, or for generic signatures of technical weakness exploits like a NOP sled. Exactly the same algorithms can be used for IDS as for signature matching in anti-virus software, along with which come the same signature updating issues.
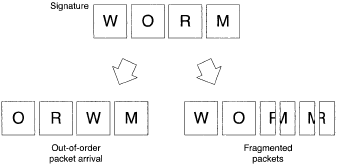
IDS signature matching is not completely straightforward, because of the properties of network traffic. A signature may not be obvious in the stream of input packets (Figure 1):
- Packets containing a signature may arrive out of order.
- A packet may he fragmented, broken into smaller pieces which may be sent out of sequence.
Network traffic can be deliberately crafted to present an IDS with these nonobvious signatures. The host machine receiving the packets will reassemble the fragments and reorder the packets. The IDS should reconstruct the correct packet stream also, but in practice may not do so correctly or may reconstruct it differently than the receiving host.
In either case, the result is exploitable. One solution is traffic normalization, which ensures that network traffic is in a canonical, unambiguous form for the IDS and other hosts by reordering and reassembling packets if necessary. Even so, a worm may defy easy signaturebased detection by being encrypted, polymorphic, or metamorphic.
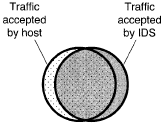
Other avenues of attack are possible against an IDS. With the exception of a host-based IDS, an IDS runs on a separate machine which may have different behavior than the hosts it protects. Figure 2 shows the results: an IDS may accept traffic that a host will reject; a host may accept traffic that an IDS will reject.
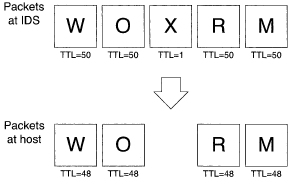
An IDS may also see traffic that never reaches a host. For example, each IP packet has a "time-to-live" counter (TTL) that is decremented once for every time the packet is sent from machine to machine during its delivery; when the counter reaches zero, the packet is discarded.
Figure 3 shows an attack exploiting the TTL counter. The traffic has been constructed so that the IDS receives extra packets that prevent it from seeing the attack signature, yet the extra packets expire due to a low TTL value before reaching the targeted host.
The fact that an IDS can detect but not block attacks is exploitable too. In the simplest case, a fast-spreading worm attacks and executes its payload before an IDS alarm is responded to.
But an IDS is a so-called fail-open system, meaning that it leaves the network accessible in the event that the IDS fails.
A more advanced attack would first overload the IDS with a denial of service, then perform the worm infection while the IDS is struggling and unable to raise an alarm.
Finally, an IDS is a real-time system. It must be able to keep up with the maximum rate of network traffic. Powerful, accurate, but high-overhead detection techniques are not suitable for use in an IDS. Taken together, all these drawbacks make an IDS yet another partial worm defense.