Protecting Windows System
Not all computer problems come from software bugs and hardware glitches. When you connect your PC to the Internet, you open up a whole new world of potential dangers—viruses, spam, computer attacks, and more.
Fortunately, it’s easy to protect your computer and your family from these dangers. All you need are a few software utilities—and a lot of common sense! A computer virus is a malicious software program designed to do damage to your computer system by deleting files or even taking over your PC to launch attacks on other systems.
A virus attacks your computer when you launch an infected software program, launching a “payload” that oftentimes is catastrophic. How do you know whether your computer system has been infected with a virus?
In general, whenever your computer starts acting different from normal, it’s possible that you have a virus. You might see strange messages or graphics displayed on your computer screen or find that normally well-behaved programs are acting erratically.
You might discover that certain files have gone missing from your hard disk or that your system is acting sluggish—or failing to start at all. You might even find that your friends are receiving emails from you (that you never sent) that have suspicious files attached.
If your computer exhibits one or more of these symptoms—especially if you’ve just downloaded a file from the Internet or received a suspicious email message—the prognosis is not good. Your computer is probably infected.
Whenever you share data with another computer or computer user, you risk exposing your computer to potential viruses. There are many ways you can share data and many ways a virus can be transmitted:
- Opening an infected file attached to an email message or instant message.
- Launching an infected program file downloaded from the Internet.
- Sharing a data CD, USB memory drive, or floppy disk that contains an infected file.
- Sharing over a network a computer file that contains an infected file.
Of all these methods, the most common means of virus infection is via email—with instant messaging close behind. Whenever you open a file attached to an email message or instant message, you stand a good chance of infecting your computer system with a virus—even if the file was sent by someone you know and trust.
That’s because many viruses “spoof” the sender’s name, thus making you think the file is from a friend or colleague. The bottom line is that no email or instant message attachment is safe unless you were expressly expecting it.
Because you’re not going to completely quit doing any of these activities, you’ll never be 100% safe from the threat of computer viruses. There are, however, some steps you can take to reduce your risk:
- Don’t open email attachments from people you don’t know—or even from people you do know, if you aren’t expecting them. (That’s because some viruses can hijack the address book on an infected PC, thus sending out infected email that the owner isn’t even aware of.)
- Don’t accept any files sent to you via instant messaging.
- Download files only from reliable file archive websites, such as Download.com and Tucows.
- Don’t execute programs you find in Usenet newsgroups or posted to web message boards or blogs.
- Don’t click links sent to you from strangers via instant messaging or in a chat room.
- Share disks and files only with users you know and trust.
- Use antivirus software—and keep it up-todate with the most recent virus definitions.
These precautions—especially the first one about not opening email attachments—should provide good insurance against the threat of computer viruses.
Disinfecting with Antivirus
Antivirus software programs are capable of detecting known viruses and protecting your system against new, unknown viruses. These programs check your system for viruses each time your system is booted and can be configured to check any programs you download from the Internet. They’re also used to disinfect your system if it becomes infected with a virus.
The most popular antivirus programs include:
- AVG Anti-Virus
- Kaspersky Anti-Virus Personal
- McAfee VirusScan
- Norton AntiVirus
- PC-cillin
- Windows Live OneCare
All of these programs do a good job—although their prices vary considerably.
For example, AVG Anti-Virus is available for free (and does a great job), Norton AntiVirus costs $39.99 for a one-year subscription, and Windows Live OneCare costs $49.95 per year—although you can use it on up to three different PCs, which makes it a real bargain for multiple-PC households.
Whichever antivirus program you choose, you’ll need to go online periodically to update the virus definition database the program uses to look for known virus files. As new viruses are created every week, this file of known viruses must be updated accordingly.
Fighting Spam
Viruses aren’t the only annoying things delivered via email. If you’re like most users, well over half the messages delivered to your email inbox are unsolicited, unauthorized, and unwanted—in other words, spam. These spam messages are the online equivalent of the junk mail you receive in your postal mailbox, and it’s a huge problem.
Although it’s probably impossible to do away with 100% of the spam you receive (you can’t completely stop junk mail, either), there are steps you can take to reduce the amount of spam you have to deal with. The heavier your spam load, the more steps you can take.
Protecting Email Address
Spammers accumulate email addresses via a variety of methods. Some use hightech methods to harvest email addresses listed on public web pages and message board postings. Others use the tried-and-true approach of buying names from list brokers.
Still others automatically generate addresses using a “dictionary” of common names and email domains. One way to reduce the amount of spam you receive is to limit the public use of your email address.
It’s a simple fact: The more you expose your email address, the more likely it is that a spammer will find it—and use it. To this end, you should avoid putting your email address on your web page, or your company’s web page.
You should also avoid including your email address in any postings you make to web-based message boards or Usenet newsgroups. In addition, you should most definitely not include your email address in any of the conversations you have in chat rooms or via instant messaging.
Another strategy is to actually use two email addresses. Take your main email address (the one you get from your ISP) and hand it out only to a close circle of friends and family; do not use this address to post any public messages or to register at any websites.
Then obtain a second email address (you can get a free one at Hotmail, Yahoo, or Gmail) and use that one for all your public activity. When you post on a message board or newsgroup, use the second address. When you order something from an online merchant, use the second address.
When you register for website access, use the second address. Over time, the second address will attract the spam; your first email address will remain private and relatively spam-free.
Blocking Spammers in Email Programs
Most email programs include some sort of spam filtering. As you might suspect, newer programs have more robust spam filters than do older programs. For example, the older Outlook Express program doesn’t even have a spam filter built in.
Instead, the program lets you manually block messages from known spammers by using the Blocked Senders List feature. When you receive a spam message in your inbox, select the message and then select Message, Block Sender. In the future, all messages from this sender will automatically be deleted.
For more robust spam fighting, you can upgrade to Microsoft Outlook. Outlook 2003 includes four levels of spam filtering, which you can access by selecting Actions, Junk E-Mail, Junk E-Mail Options.
The four levels are Low (blocks the obvious spam messages), High (blocks most spam messages, but might also block some nonspam email), Safe Lists Only (blocks all email except from people on your Safe Senders List), and No Automatic Filtering (turns off the spam filter).
Outlook 2007 features an even more advanced junk email filter, as does Windows Mail, the email program included with Windows Vista. Bottom line: The newer the email program, the better its spam-fighting capabilities. This may be reason enough to upgrade from Outlook Express in Windows XP to Windows Mail in Windows Vista, or from Outlook 2003 to Outlook 2007.
Using Anti-Spam Software
If the amount of spam in your inbox becomes particularly onerous, you might want to consider using an anti-spam software program. Most anti-spam software uses some combination of spam blocking or content filtering to keep spam messages from ever reaching your inbox; their effectiveness varies, but they will decrease the amount of spam you receive to some degree.
The most popular anti-spam software includes:
In addition, many antivirus and content filtering programs also include anti-spam modules. If you’re already using an antivirus program or security suite, check whether it offers spam email filtering.
Phishing Scams
Phishing is a technique used by online scam artists to steal your identity by tricking you into disclosing valuable personal information, such as passwords, credit card numbers, and other financial data. If you’re not careful, you can mistake a phishing email for a real one—and open yourself up to identity theft.
A phishing scam typically starts with a phony email message that appears to be from a legitimate source, such as your bank, eBay, or PayPal. When you click the link in the phishing email, you’re taken to a fake website masquerading as the real site, complete with logos and officiallooking text.
You’re encouraged to enter your personal information into the forms on the web page; when you do so, your information is sent to the scammer, and you’re now a victim of identity theft.
When your data falls into the hands of criminals, it can be used to hack into your online accounts, make unauthorized charges on your credit card, and maybe even drain your bank account.
Until recently, the only guard against phishing scams was common sense. That is, you should never click through a link in an email message that asks for any type of personal information—whether that be your bank account number or eBay password.
Even if the email looks official, it probably isn’t; legitimate institutions and websites never include this kind of link in their official messages. Instead, you should access your personal information only by using your web browser to go directly to the website in question.
Don’t link there! This all changes in Windows Vista, which includes a new feature called the Microsoft Phishing Filter. This filter works within both Windows Mail and Internet Explorer 7 and compares all the links in your Windows Mail email messages to an online list of known phishing websites.
If the link matches a fraudulent site, Windows Mail displays a warning message at the top of the message. If you attempt to click a link to a known phishing site, the Microsoft Phishing Filter blocks access to the site, changes the Address Bar to red, navigates to a neutral page, and displays a warning message.
If you attempt to click a link to a site that is not on the list of known fraudulent sites but behaves similarly to such sites, the Microsoft Phishing Filter changes the Address Bar to yellow and cautions you about potentially suspicious content. But whether you’re using Windows Mail or any other email program, use your head.
Don’t click through suspicious email links, and don’t give out your personal information and passwords unless you’re sure you’re dealing with an official (and not just an official-looking) site!
Spyware
Another growing online nuisance is the proliferation of spyware programs. These are programs that install themselves on your computer and then surreptitiously send information about the way you use your PC to some interested third party. Spyware typically gets installed in the background when you’re installing another program.
One of the biggest sources of spyware are peer-to-peer musictrading networks (not legitimate online music stores, such as the iTunes Store); when you install the file-trading software, the spyware is also installed. Having spyware on your system is nasty, almost as bad as being infected with a computer virus.
Some spyware programs will even hijack your computer and launch pop-up windows and advertisements when you visit certain web pages. If there’s spyware on your computer, you definitely want to get rid of it. Unfortunately, most antivirus programs won’t catch spyware because spyware isn’t a virus.
To track down and uninstall these programs, then, you need to run an antispyware utility, such as Windows Defender, which is included free with Windows Vista—and available as a free download for Windows XP users.
Here are some of the best of these spyware fighters:
In addition, some of the major Internet security suites, such as Norton Internet Security and the McAfee Internet Security Suite, include anti-spyware modules. Check the program’s feature list before you buy.
Computer Attacks
Connecting to the Internet is a two-way street—not only can your PC access other computers online, but other computers can also access your PC. Which means that, unless you take proper precautions, malicious hackers can read your private data, damage your system hardware and software, and even use your system (via remote control) to cause damage to other computers.
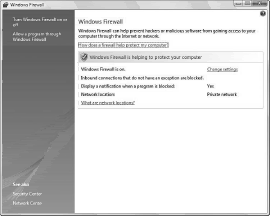
You protect your system against outside attack by blocking the path of attack with a firewall. A firewall is a software program that forms a virtual barrier between your computer and the Internet. The firewall selectively filters the data that is passed between both ends of the connection and protects your system against outside attack.
Using the Windows Firewall
If you’re running Windows Vista or Windows XP, you already have a firewall program installed on your system. The Windows Firewall is activated by default, although you can always check to make sure that it’s up and working properly. In Windows Vista, open the Control Panel and select Security, Windows Firewall (see Figure below).
In Windows XP, open the Control Panel and go to the Windows Security Center; all Windows security settings are visible there.
Using Third-Party Firewall Software
For most users, the Windows Firewall is more than enough protection against computer attacks. That said, a number of third-party firewall programs also are available, most of which are more robust and offer more protection than Windows’ built-in firewall.
The best of these programs include:
Inappropriate Content
The Internet contains an almost limitless supply of information on its tens of billions of web pages. Although most of these pages contain useful information, it’s a sad fact that the content of some pages can be quite offensive to some people—and that there are some Internet users who prey on unsuspecting youths.
As a responsible parent, you want to protect your children from any of the bad stuff (and bad people) online, while still allowing access to all the good stuff. How do you do this?
Using Content-Filtering Software
If you can’t trust your children to always click away from inappropriate web content, you can choose to install software on your computer that performs filtering functions for all your online sessions.
These safe-surfing programs guard against either a preselected list of inappropriate sites or a preselected list of topics—and then block access to sites that meet the selected criteria. Once you have the software installed, your kids won’t be able to access the really bad sites on the Web.
The most popular filtering programs include the following:
In addition, many of the big Internet security suites (such as those from McAfee and Norton/Symantec) offer built-in content-filtering modules.
Kids-Safe Searching
If you don’t want to go to all the trouble of using content-filtering software, you can at least steer your children to some of the safer sites on the Web. The best of these sites offer kid-safe searching so that all inappropriate sites are filtered out of the search results. The best of these kids-safe search and directory sites include:
- AltaVista—AV Family Filter (go to the Settings page and click the Family Filter link)
- Ask for Kids
- Fact Monster
- Google SafeSearch (go to the Preferences page and then choose a SafeSearch Filtering option)
- Yahooligans!
Encouraging Safe Computing
Although your using content-filtering software and kids-safe websites are good steps, the most important thing you can do, as a parent, is to create an environment that encourages appropriate use of the Internet.
Nothing replaces traditional parental supervision, and at the end of the day, you have to take responsibility for your children’s online activities. Provide the guidance they need to make the Internet a fun and educational place to visit—and your entire family will be better for it.
Here are some guidelines you can follow to ensure a safer surfing experience for your family:
- Make sure that your children know never to give out any identifying information (home address, school name, telephone number, and so on) or to send their photos to other users online.
- Provide each of your children with an online pseudonym so they don’t have to use their real names online.
- Don’t let your children arrange face-to-face meetings with other computer users without parental permission and supervision. If a meeting is arranged, make the first one in a public place and be sure to accompany your child.
- Teach your children that people online might not always be who they seem; just because someone says that she’s a 10-year-old girl doesn’t necessarily mean that she really is 10 years old, or a girl.
- Consider making Internet surfing an activity you do together with your younger children—or turn it into a family activity by putting your kids’ PC in a public room (such as a living room or den) rather than in a private bedroom.
- Set reasonable rules and guidelines for your kids’ computer use. Consider limiting the number of minutes/hours they can spend online each day.
- Monitor your children’s Internet activities. Ask them to keep a log of all websites they visit; oversee any chat sessions they participate in; check out any files they download; even consider sharing an email account (especially with younger children) so that you can oversee their messages.
- Don’t let your children respond to messages that are suggestive, obscene, belligerent, or threatening—or that make them feel uncomfortable in any way. Encourage your children to tell you if they receive any such messages, and then report the senders to your ISP.
- Install content-filtering software on your PC, and set up one of the kid-safe search sites (discussed earlier in this section) as your browser’s start page.
Teach your children that Internet access is not a right; it should be a privilege earned by your children and kept only when their use of it matches your expectations.